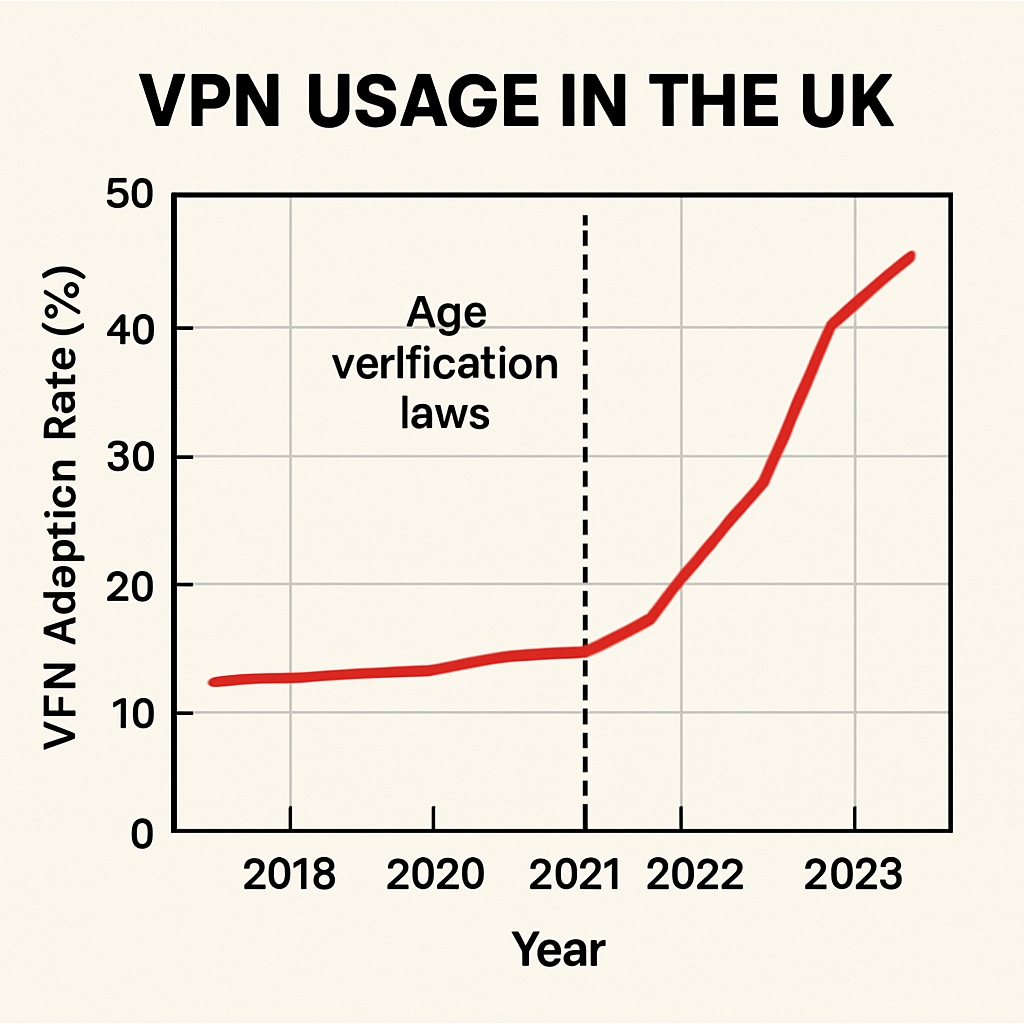
The implementation of the UK’s age verification policy has stirred significant debate among internet users and privacy advocates. This regulation requires websites hosting adult content to verify users’ ages, often through government-approved platforms. While the policy aims to protect minors, it has inadvertently sparked concerns about data collection and user privacy. As a result, many individuals are adopting measures like Virtual Private Networks (VPNs) to circumvent these restrictions and safeguard their personal information.
Understanding the UK Age Verification Policy
The UK’s age verification policy, introduced under the Digital Economy Act, mandates that platforms hosting age-sensitive content, such as adult websites, enforce stringent access controls. Users are required to confirm their age using identification methods like credit card details or government-issued IDs. The law intends to restrict underage access to adult material and promote safer internet usage.
However, this regulation raises critical questions regarding user privacy. By submitting sensitive information, individuals risk exposing personal data to potential breaches or misuse. Furthermore, critics argue that the policy’s centralized verification systems could inadvertently create targets for cyberattacks.
Why Users Are Turning to VPNs
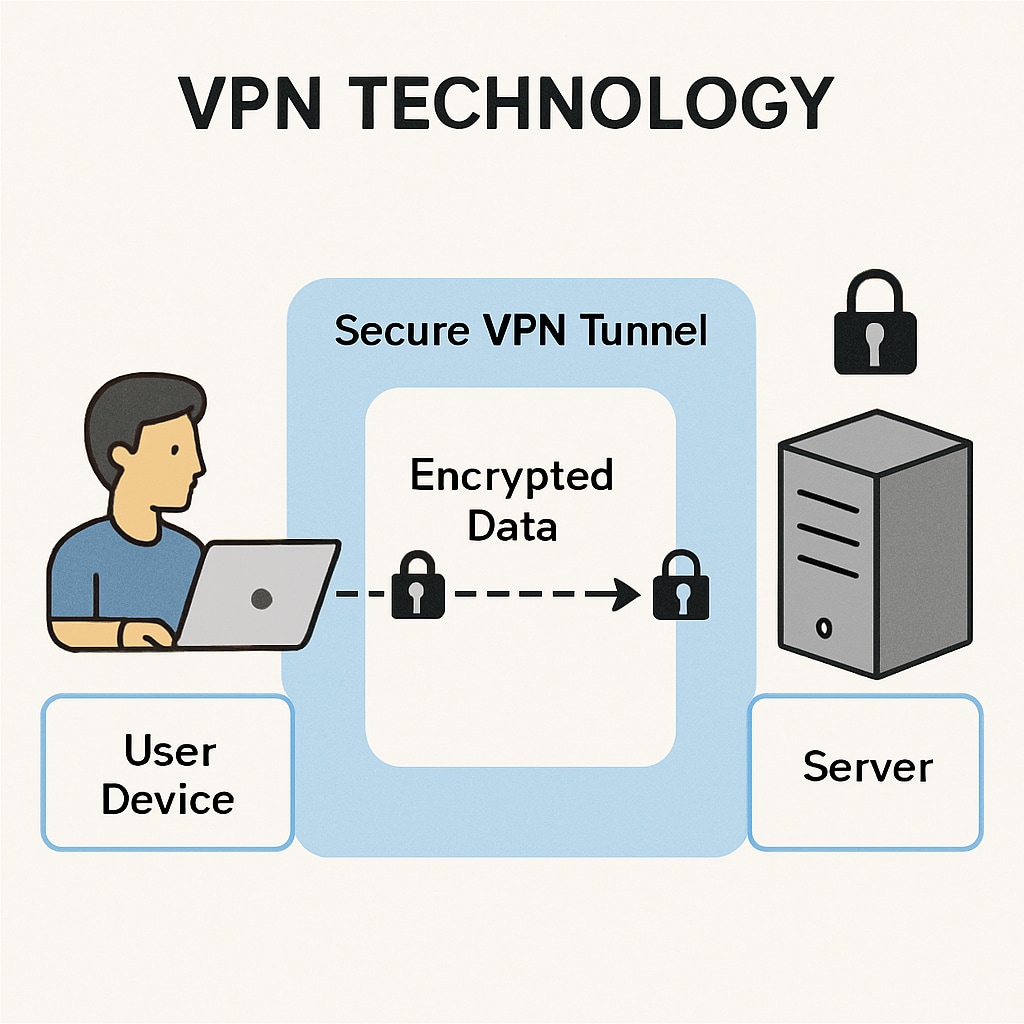
Faced with privacy concerns, many UK internet users have started relying on VPNs (Virtual Private Networks) to bypass the age verification process. VPNs encrypt user data and reroute internet traffic through servers in different locations, allowing individuals to access restricted content without exposing their identities or personal information.
VPNs provide several benefits, including:
- Anonymity: Users can hide their IP addresses, making it difficult for websites or governments to track their online activities.
- Bypassing restrictions: By connecting to servers outside the UK, users can access content without triggering local verification requirements.
- Enhanced security: VPNs protect data from interception, ensuring sensitive information remains private.
However, VPN usage is not without challenges. Some platforms actively block VPN traffic, and free VPNs may compromise user security by logging data or displaying intrusive ads.
Potential Impacts of the Age Verification Law
The introduction of the age verification law has broader implications beyond privacy concerns. For example:
- Shift in user behavior: Many users are opting for privacy-focused tools and services, such as VPNs, to navigate restrictions.
- Economic effects: VPN providers have reported a surge in subscriptions, highlighting a growing market for privacy solutions.
- Legal challenges: Privacy advocates may challenge the law’s scope and implementation, arguing that it infringes on individual rights.
The debate also underscores the importance of balancing safety with privacy in policymaking. While protecting minors is a valid goal, it should not come at the cost of compromising user data security.
The Future of UK Internet Regulations
As technology evolves, governments worldwide face the challenge of regulating online content without infringing on fundamental rights. In the UK, the controversy surrounding age verification laws highlights the need for transparent and privacy-conscious solutions. Policymakers must consider alternative approaches, such as decentralized verification systems or blockchain technology, to ensure both safety and anonymity.
In addition, public education about online privacy and responsible internet use can empower individuals to make informed decisions. Collaboration between governments, tech companies, and privacy advocates will also play a crucial role in shaping future regulations.
Ultimately, the ongoing debate surrounding the UK’s age verification policy serves as a reminder of the delicate balance between internet safety and privacy. As users increasingly turn to VPNs and other tools to protect their anonymity, it is clear that privacy concerns will remain a central issue in the digital age.
Readability guidance: Short paragraphs and lists summarize key points effectively. Transition words like “however” and “in addition” ensure readability. Images are strategically placed to enhance the reader’s understanding of VPN usage and technology.


