The introduction of age verification policies under UK regulations has sparked significant changes in online user behavior, particularly concerning privacy. Many individuals are now turning to VPNs (Virtual Private Networks) to shield their personal data and bypass restrictions, raising questions about the balance between safety, privacy, and accessibility in the digital age. This article will explore the implications of these policies and how they are reshaping user privacy practices.
The Role of Age Verification in UK Policies
In recent years, the UK government has implemented stricter measures to regulate online content, including mandatory age verification for accessing certain websites. These rules aim to protect minors from inappropriate material and ensure compliance with digital safety standards. However, this approach has raised concerns about how user data is collected, stored, and potentially exploited.
Age verification often requires users to submit sensitive information, such as documents proving their age or identity. While these measures may enhance safety, they have also triggered privacy concerns, as users worry about the potential misuse or breach of their personal data. As a result, individuals are increasingly seeking ways to navigate these restrictions without compromising their privacy.

VPN Usage: A Growing Response to Privacy Concerns
One of the most notable responses to these policies has been the rise in VPN usage. VPNs allow users to mask their location and encrypt their internet activities, enabling them to bypass age verification systems and access restricted websites anonymously. For example, a VPN can reroute a user’s internet connection through servers in countries with less stringent regulations, effectively circumventing UK-specific requirements.
While VPNs empower users to maintain privacy and access content freely, they also pose challenges for regulators. VPN usage can make it difficult to enforce compliance with age verification rules, potentially undermining the intended protective measures. This dynamic highlights the tension between safeguarding minors and respecting individual privacy rights.
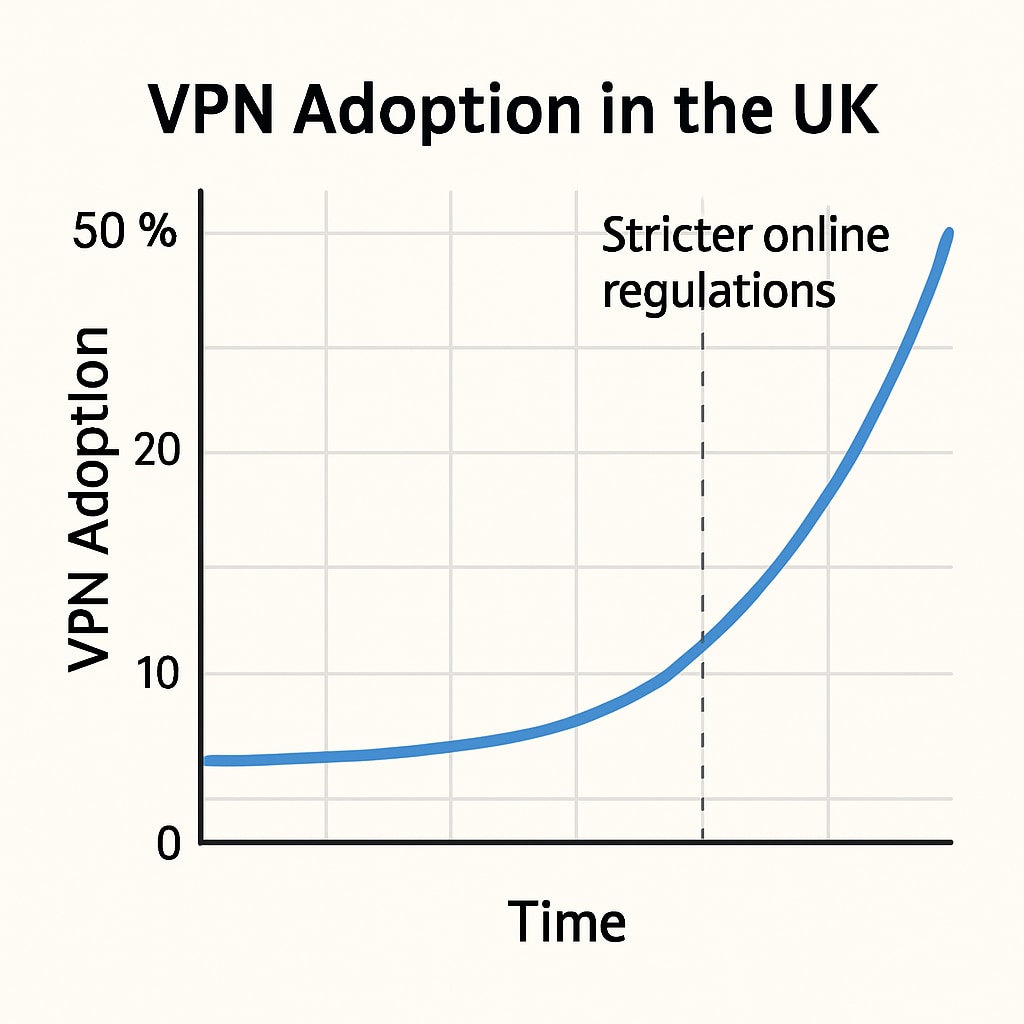
Broader Implications for Privacy and Security
The widespread adoption of VPNs and other privacy tools reflects broader concerns about digital security. Many users fear that mandatory age verification could set a precedent for invasive online monitoring and surveillance. Additionally, the risk of data breaches adds another layer of complexity, as even secure systems are vulnerable to cyberattacks.
For regulators, balancing safety and privacy requires careful consideration. Transparency in how user data is handled, robust security measures, and clear guidelines for compliance are essential to address public concerns. On the user side, the growing reliance on VPNs underscores the importance of educating individuals about digital safety practices and the potential risks associated with unregulated privacy tools.
Conclusion: Navigating the Privacy Landscape
The UK’s age verification regulations have undoubtedly sparked important conversations about online safety and privacy. While these measures aim to protect vulnerable populations, the unintended consequences—such as increased VPN usage—illustrate the complexities of implementing such policies. Moving forward, a balanced approach that prioritizes both safety and privacy will be crucial in shaping the future of digital regulation.
As users adapt to these changes, it is vital to stay informed about the tools and strategies available for maintaining privacy while complying with legal requirements. For further reading on digital privacy and security, explore authoritative resources like VPNs on Wikipedia and Internet Privacy on Britannica.
Readability guidance: This article uses short paragraphs, active voice, and transitions to ensure clarity. Lists are used to summarize key points, and technical terms are explained for accessibility.


